Block TCP Port 445: Top 3 Easy Methods for Windows 11, 10, 7
- Unveiling WannaCry: An Overview of the Cyberattack
- Port 445 vs. Port 139: Understanding the Difference
- How to Check if Port 445 Is Open or Not
- How to Close Port 445 in Windows 11, 10, 7
- How to Block Port 445 in Windows Firewall
- How to Close TCP Port 445 Opened by System on Windows 7 via CMD
- How to Block TCP Port 445 via RegEdit
- Surviving WannaCry and Petya: Essential Tips for Staying Safe
- In the End: Protecting Your System from Cyber Threats
Unveiling WannaCry: An Overview of the Cyberattack
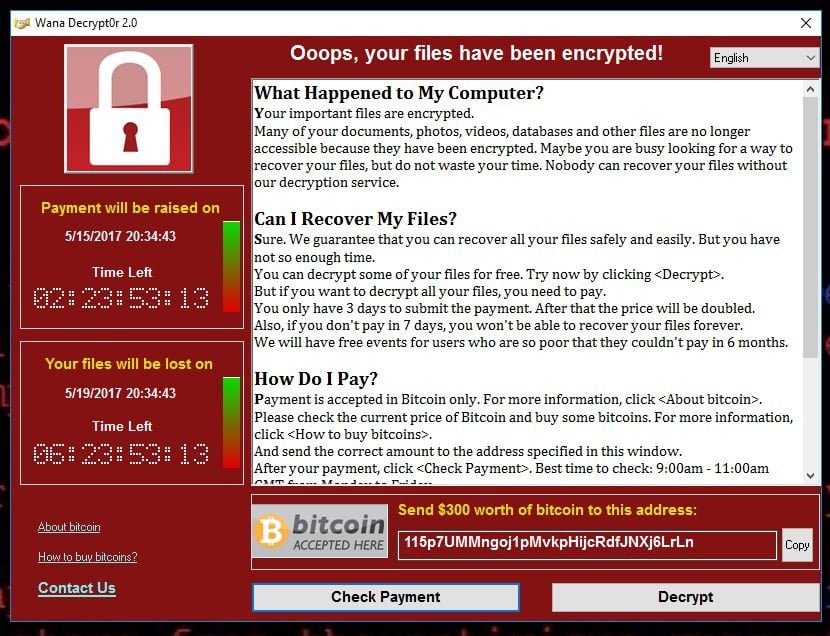
WannaCry, a highly contagious ransomware, has been wreaking havoc on computers worldwide since May 12, 2017, encrypting important files and documents and demanding $300 to $600 in virtual Bitcoin currency in exchange for the decryption key. Unfortunately, no effective decryption methods have been found, leaving victims with no choice but to wait for a cure. However, there are some preventive measures that can be taken to avoid infection and make things better.
The WannaCry and Petya variants of malware infect hard drives through TCP port 445, which is opened during system installation, similar to port 139. To block port 445 in Windows 7, 10, and XP, follow these simple steps. However, before doing so, it's worth understanding what TCP port 445 is used for.
Port 445 vs. Port 139: Understanding the Difference
Ports 445 and 139 are Windows ports used for NetBIOS name resolution and SMB, serving Windows File and Printer Sharing.
In Windows 2000, Microsoft replaced the traditional SMB transport with a new one that uses TCP and UDP on port 445, rather than the older ports 137, 138, and 139. This means that keeping ports 445 and 139 open can expose your hard drives to unauthorized access, including deletion, formatting, and virus implantation.
Closing port 445 will block file system data transfer and break group policy, resulting in loss of network browsing capabilities beyond the intranet network.
👉 How to Check If Port 445 Is Open or Not
👉 How to Close Port 445 in Windows 11, 10, 7
👉 Surviving WannaCry and Petya: Essential Tips for Staying Safe🔥
How to Check if Port 445 Is Open or Not
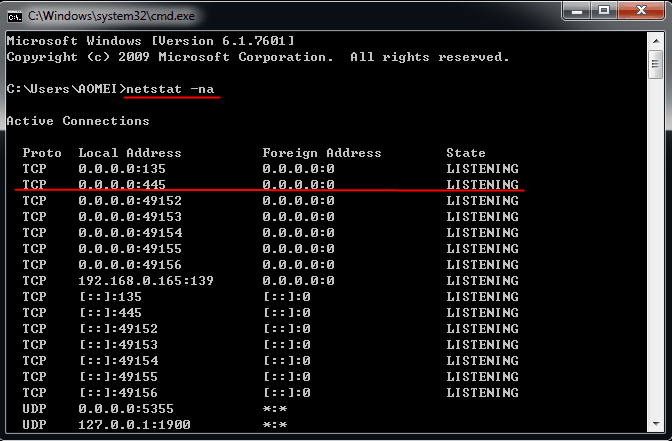
To check if port 445 is open on your Windows host, start the Command Prompt by pressing the Windows key + R, typing "cmd", and pressing Enter. Then, type "netstat -na" and press Enter. This command will scan all connected ports and display them in numerical format.
The picture will appear in a short time. Moving your mouse to the top will display the IP address of 445. The last column shows the status as "LISTENING", indicating that the TCP port 445 is open.
How to Close Port 445 in Windows 11, 10, 7
Closing port 445, which has been a hotbed for malware and was exploited in the WannaCry attack, is now urgent. There are three simple methods to disable this port in Windows 10, 7, and XP, making it easy to follow. These methods can be used to prevent potential malware attacks and ensure the security of your system. Let's explore them one by one.
How to Block Port 445 in Windows Firewall
The first method is the easiest one and is suitable for almost every Windows user.
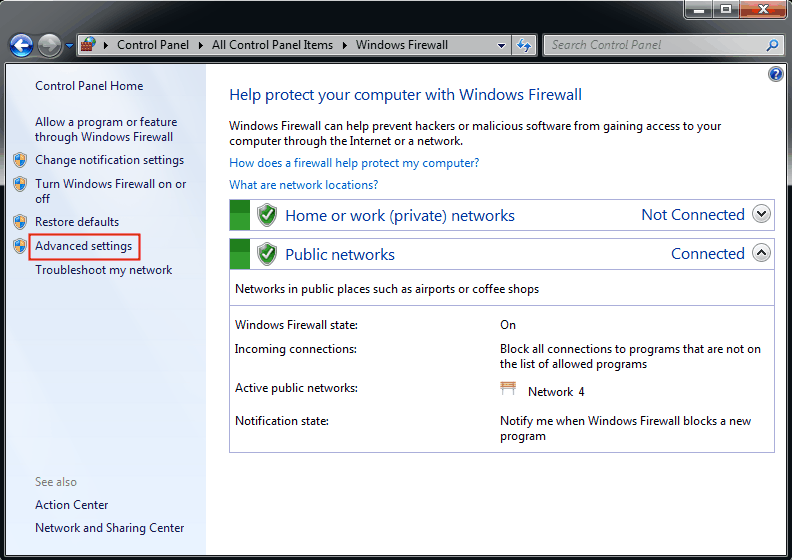
1. To access the Windows Firewall settings, go to Start, then click on Control Panel, and from there, find the Windows Firewall option. On the left side, click on Advanced settings.
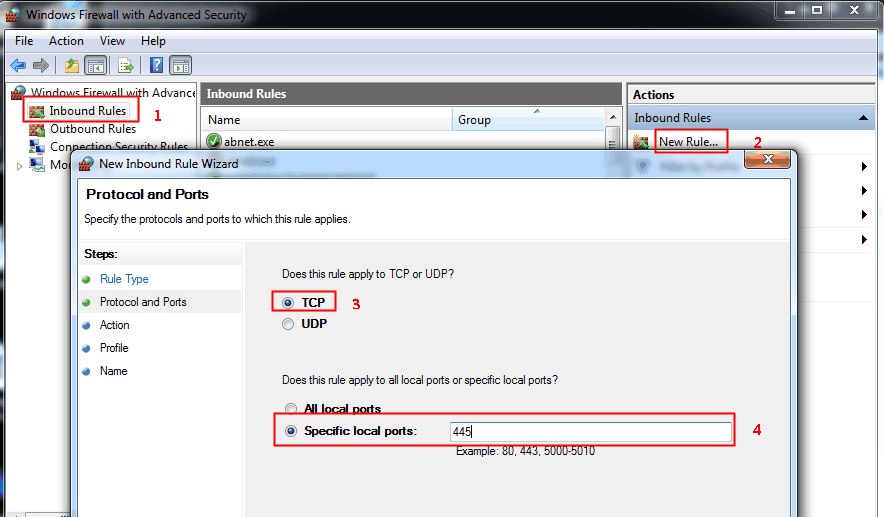
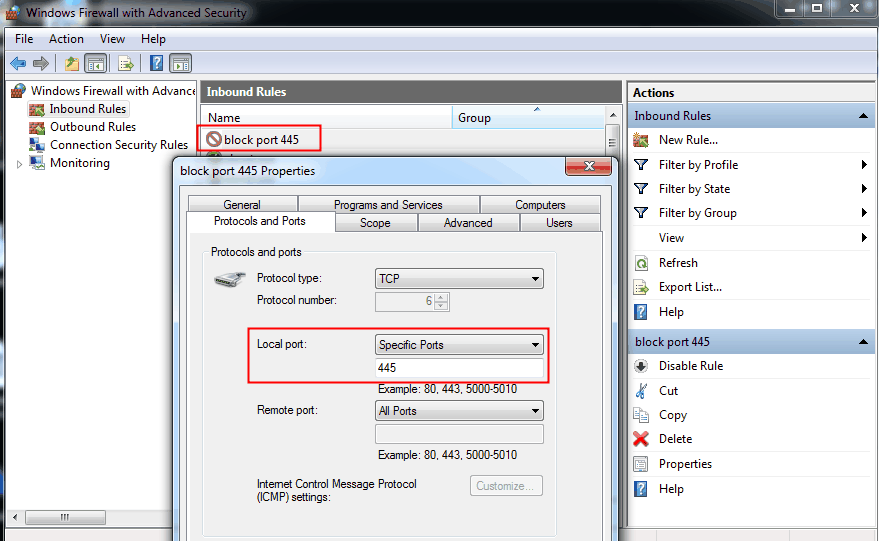
2. To create a new inbound rule, go to Inbound Rules, click New rule, and then select Port from the options. Next, choose TCP and select Specific local ports. In the box provided, type 445 and click Next to proceed.
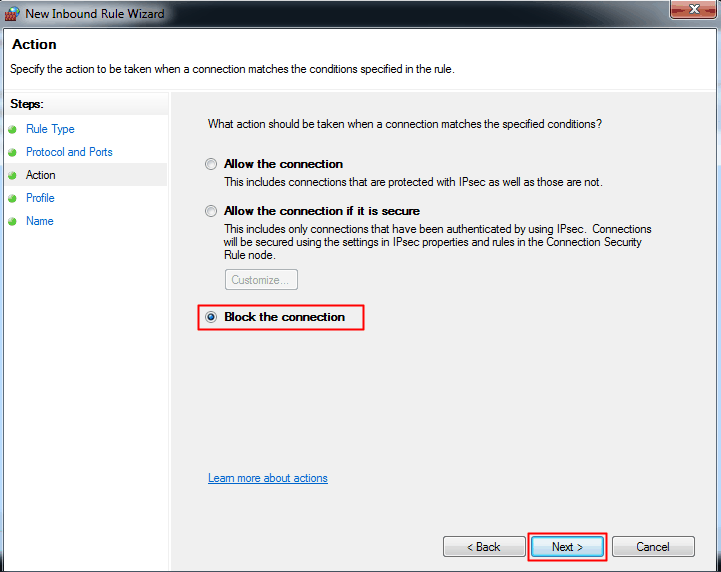
3. To block the connection, select "Block the connection" and click "Next". Then, check the three boxes and click "Next" again. Finally, enter a name and description as desired and click "Finish".
4. To check if you have created the rule, go to Properties > Protocols and Ports > Local Port.
For those who prefer command line operations, there's another way to stop port 445 using Windows Firewall, which might be their preferred method.
How to Close TCP Port 445 Opened by System on Windows 7 via CMD
Command line operations are immediate and irreversible, so users unfamiliar with this interface should exercise caution.
1. To run the Command Prompt as an administrator, you can type "cmd" in the search box, right-click the "cmd" from the list, and select "Run as administrator".
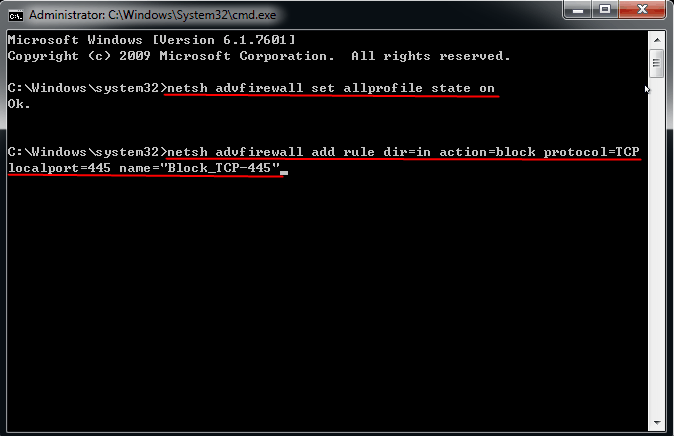
2. Input: netsh advfirewall set allprofile state on and press Enter.
3. The command "netsh advfirewall firewall add rule dir=in action=block protocol=TCP localport=445 name="Block_TCP-445"" is used to block incoming TCP traffic on port 445. When executed in Command Prompt, it adds a new rule to the Windows Firewall to block any incoming connections on port 445.
Some users have reported that the first two methods do not work on their computers, and the port 445 remains in "LISTENING" mode in the Command Prompt. In such cases, a third method can be tried, which is also relatively simple.
How to Block TCP Port 445 via RegEdit
Modifying the system's registry can also help protect against WannaCry ransomware, but it requires caution, as the registry is a database for system programs and applications, and deleting important files can cause issues. It's recommended to backup the registry before making any changes.
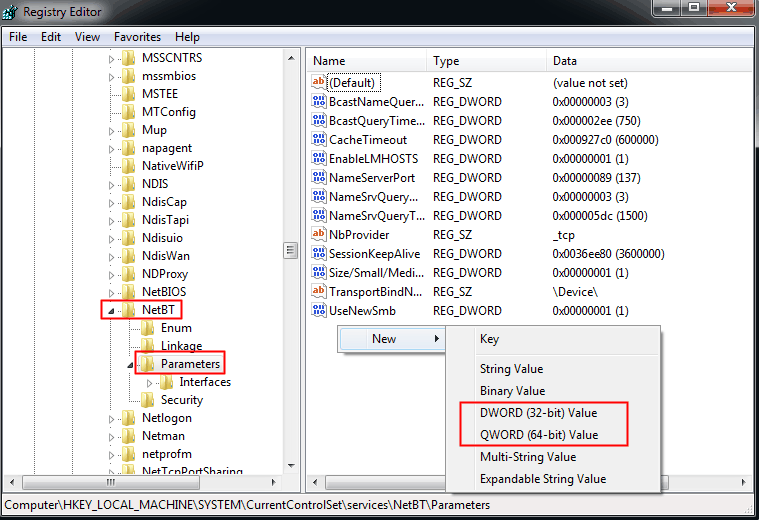
1. To open the Registry Editor, press the Windows key + R to open the Run box, type "regedit" and press Enter.
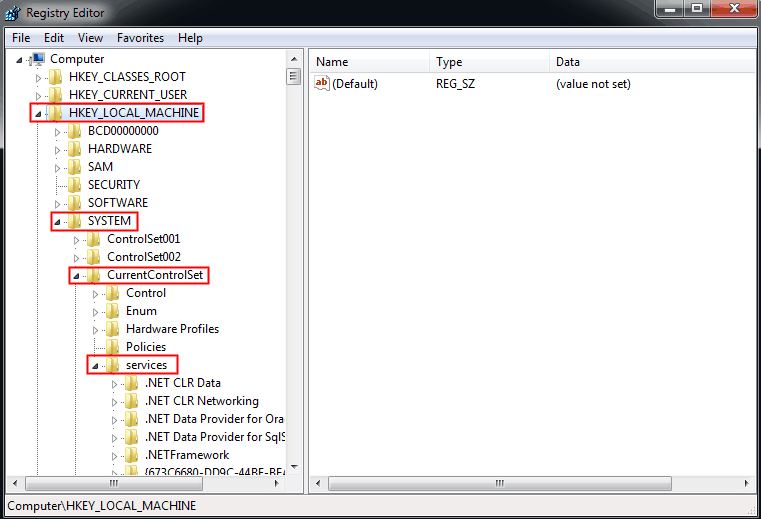
2. Navigate to the path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\NetBT\Parameters
3. To add a new DWORD or QWORD value to the registry, right-click a blank area and select "New," then choose either "DWORD (32-bit) Value" or "QWORD (64-bit) Value" based on your system's architecture.
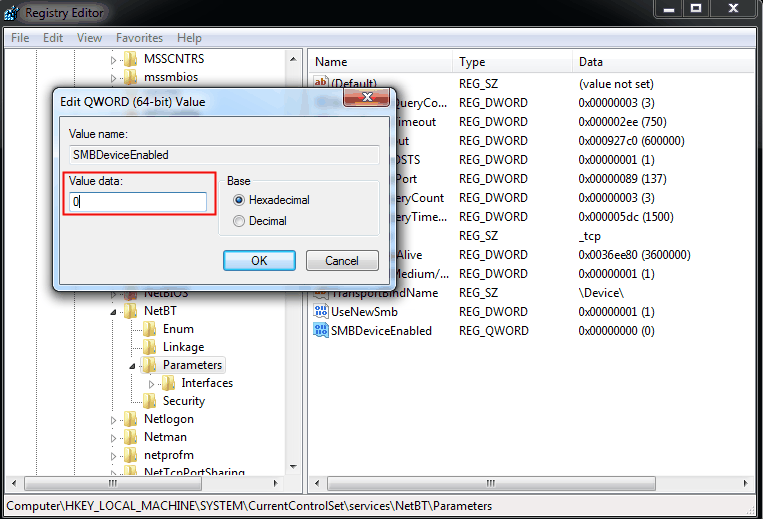
4. Rename the new value to SMBDeviceEnabled. Right click it and select Modify. Change Value data from 1 to 0. Click OK to confirm.
This method is effective and can be applied to almost every computer user. If you follow the steps strictly, no mistakes will be made. It's also worth noting that disabling the Windows Server service can help strengthen protection against the WannaCry cyber attack.
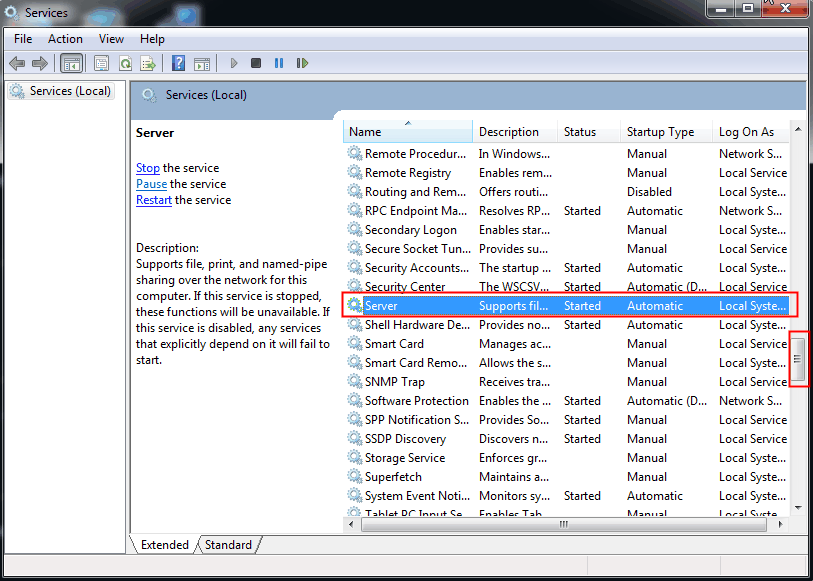
1. Type "services.msc" in Run box to open Windows Services.
2. To access the server, find it in the service events and double click on it, which is typically located at the middle of the service events.
3. To disable the Java plug-in, in Internet Explorer, click Tools and then click Internet Options. In the Internet Options window, click the Security tab, click Custom Level, click Enable or disable ActiveX controls and plug-ins and select Disable from the drop-down list, and then click OK.
Tips:
To block ports 139, 135, 137, and 138, follow the same steps as blocking port 445, but replace 445 with each of these ports in the steps. Closing all of them temporarily is recommended.
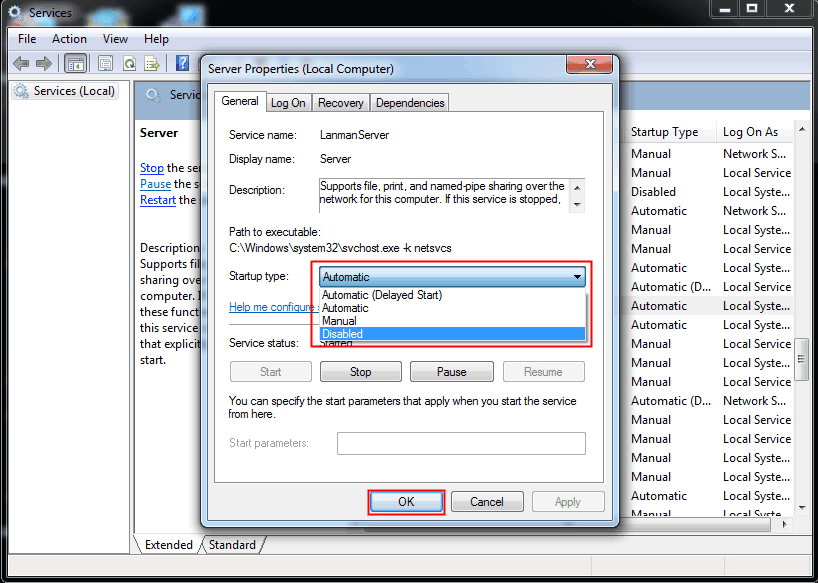
To enable port 445 in Windows 7, simply delete the newly created rule in Windows Firewall, or change the value data from 0 to 1 in Registry Editor, or delete the value in Registry Editor, or switch the Disabled option to Automatic in Server Properties. This will allow future access to port 445.
Surviving WannaCry and Petya: Essential Tips for Staying Safe
Disabling TCP port 445 and other high-risk ports is crucial in preventing ransomware attacks, but there's more to do. Security experts recommend taking additional steps to protect against these malicious threats, which can be devastating to individuals and organizations.
1. If you're unsure whether your computer has been hacked, it's recommended to disconnect it from the network first and then boot it up. This can help prevent any potential hackers from accessing your data or taking control of your device.
2. Install Windows patches and anti-virus software.
3. Do not click suspicious links in emails or on websites.
4. To protect yourself from WannaCry ransomware, back up all your important files and data using a reliable backup software like Qiling Disk Master Standard, which is free. This will ensure that your files are safe even if your computer fails to boot. Additionally, creating bootable media can be a lifesaver in case your computer is unable to start up normally.
5. Backup on a regular basis.
In the End: Protecting Your System from Cyber Threats
The WannaCry ransomware attack was a global cyberattack that caught everyone's attention. To combat malicious hackers, we need to be proactive and prepared. While blocking ports like 445 can help remedy the situation after an attack, it's also essential to schedule regular backups for crucial data. This way, even if data is lost or compromised, having an exact copy can prevent panic and minimize the impact of future attacks.
Protecting your PC's data is crucial, but it's not the only thing that needs protection. Your system, disk, and partition also require safeguarding to prevent potential harm. To ensure comprehensive protection, consider using a free backup software like Qiling Disk Master to safeguard your important files and data.
You can backup any items you want and enable schedule backups to continuously protect your system and data. To avoid backup disk full, consider enabling high compression level, incremental and differential backups, and backup scheme according to your situation. Note that differential backup and backup scheme are features available on the professional version or higher.
Related Articles
- Can I Still Use Windows 7 After 2020 and Get Security Updates?
Can I still use Windows 7 after 2020? Definitely, you could use it as before but you need to do so at your own risk. So please learn more about Windows 7 end of life extended and make your decision. - Remove Ransomware Virus WannaCry in Windows 7 and Restore Files
If you are looking for a way to remove ransomware virus and restore files, please continue to read, learn 3 effective methods and how to prevent it in the future.