Petya Ransomware Removal and Protection
A new ransomware virus, Petya, has been reported on June 27, 2017, marking the third major ransomware attack in two months, following WannaCry and EternalRocks. This has led some to consider it a "season" for seeding ransomware viruses.
- About Petya Malware
- How Does Petya Malware Infect Your Computer?
- Petya Ransomware Removal
- How to Protect Yourself from Petya Ransomware Virus
About Petya Malware
Petya, also known as Petna or Pneytna, is a ransomware that spreads through network exploits, specifically targeting the Windows ExternalBlue vulnerability, and demands $300 in Bitcoin. The malware has infected numerous organizations in Europe and the US, including WPP, Mondelez, DLA Piper, and Maersk, encrypting their data. While it shares some similarities with WannaCry, Petya is not actually a variant of it, but rather a distinct threat with its own pros and cons.
Pros: The Petya ransomware virus attacks computers through a combination of methods, including the Windows ExternalBlue vulnerability and two administrative tools, PSEXEC or WMIC. It attempts to exploit the first option, and if that fails, it will try the other way, showcasing a more effective spreading mechanism than WannaCry.
Cons:The Petya ransomware virus has a flawed payment mechanism, using the same payment address for all victims, making it easily traceable, and a single email address for communication with hackers that has already been suspended, rendering payment and communication impossible.
Petya malware has more targeted attacks, focusing on large companies or organizations. It spread through a software update mechanism in an accounting program used by Ukrainian companies working with the government, mainly affecting Ukrainian organizations such as state power utilities, government, and banks. The virus spreads internally within networks but not externally, making it easier to control.
How Does Petya Malware Infect Your Computer?
Once Petya ransomware infects your computer, it can take anywhere from 10 to 60 minutes before it starts encrypting your data. During this time, the computer will reboot, providing a brief window of opportunity to remove the malware. To achieve this, simply switch off the power and disconnect from the internet while the computer is restarting, and you can prevent further encryption of your files.
If your computer successfully reboots after a power off, the Petya ransomware virus will check for the read-only file C:\Windows\perfc.dat. If it finds this file, it won't encrypt personal files. Creating this file in your system files may prevent the attack, although this is not a 100% guarantee.
Petya Ransomware Removal
If you've been infected with Petya malware and your files are encrypted, you can try using antivirus software to remove the malware. Alternatively, you can rescue your data by backing them up or moving them to a safe location while booting from a rescue media.
To create a bootable media, find an available USB drive with no important data on it or whose crucial data has been backed up. Insert it into an unaffected computer, and follow the necessary steps to turn it into a bootable device, such as using a tool like Rufus or the built-in USB Creator in Windows.
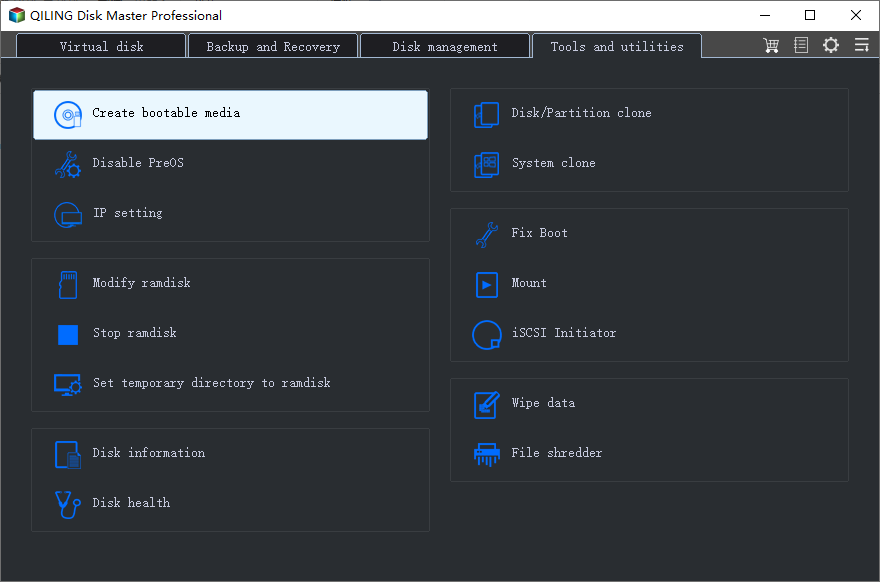
1. Download, install and open Qiling Disk Master Standard on the unaffected machine. When it opens, select Tools > Create Bootable Media.
Tip: If your computer is running an old system like Windows 7/Vista/XP, you may download the Windows ADK/AIK first.
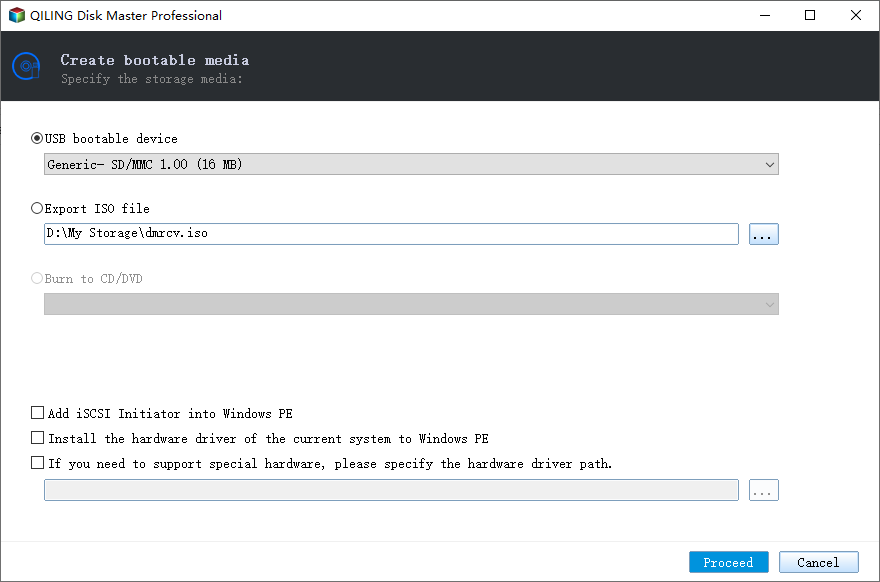
2. Choose "USB Boot Device" and click "Next".
3. Wait for it to be finished and pull out the USB flash drive.
Tip: When creating the bootable USB, Qiling Disk Master is automatically installed on the device. This allows you to directly use the USB to boot up the infected computer and then remove the Petya ransomware.
4. Connect a bootable USB to the infected machine, reboot it, and enter the BIOS before it boots into its own system, changing the boot sequence to boot from the USB instead.
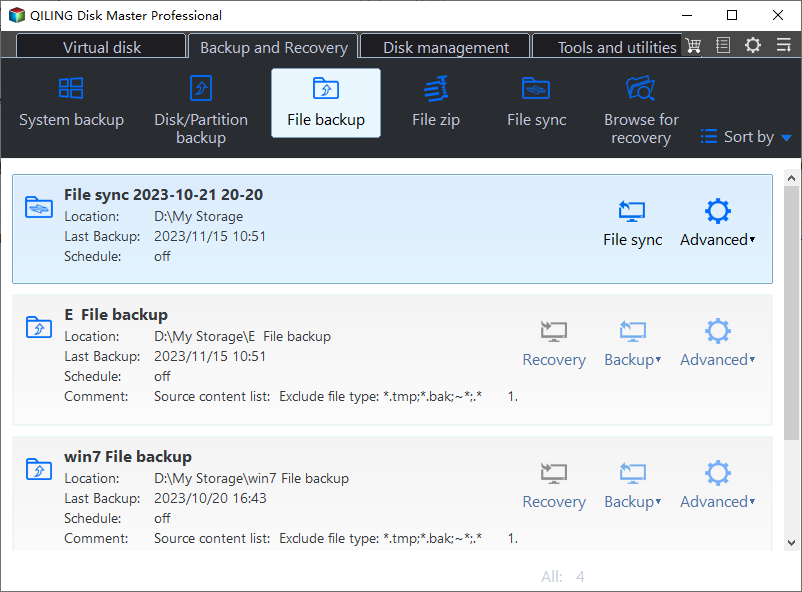
5. When Qiling Disk Master boots from the USB disk, it will automatically open. Select "File Backup" to proceed, or choose "Partition Backup" if you want to back up a non-system partition's whole data.
6. Choose all the files you want to move out of the infected computer, such as important documents, photos, and videos, and transfer them to an external drive or a cloud storage service like Google Drive or Dropbox, to prevent any potential data loss.
7. To create a backup of the infected computer, insert an external storage device, such as a USB drive, to serve as a data backup destination. The backup image can be saved directly onto this external device.
8. To proceed, wait for the backup to be completed. Then, remove both the bootable USB and the external image storage. After that, restore the backed up files to a working computer to further investigate the Petya ransomware decrypt.
How to Protect Yourself from Petya Ransomware Virus
To prevent Petya malware infection, similar to defending against WannaCry, you can take the following actions: patch Windows systems to fix the EternalBlue vulnerability and disable the two Windows administrative tools that Petya exploits. This will prevent the malware from spreading.
1. Disconnect the Network and block ports 445 and 139 to prevent further infection. To do this, go to the Control Panel, click on Advanced settings, then Inbound Rules, and create a new rule.
2. Make a backup of your key files to an external device, network share, NAS, or cloud drive, and use Qiling Disk Master Free to assist with the backup process.
3. Get a reliable antivirus software such as Windows Defender Advanced Threat Protection, Symantec, or Kaspersky, which have been updated to detect and protect against future Petya ransomware attacks.
4. Install the vulnerability patch released by Microsoft in March and keep Windows up to date.
5. Form a good habit of avoid opening unsafe websits.
Conclusion and Warning
Some security researchers believe Petya is a destructive malware, disguised as ransomware, specifically targeting the Ukrainian government. This raises the question of what would happen if terrorists were to use cyber weapons, such as ransomware, malware, or viruses, instead of physical ones. If that were the case, there would be no physical harm, but significant financial losses, paralyzed public services, and leaked sensitive information. What then?
Antivirus work is not just the responsibility of government network security centers or network operators, but also a duty of every netizen, contributing to a safe and clear network environment for all.
Related Articles
- Remove Ransomware Virus WannaCry in Windows 7 and Restore Files
If you are looking for a way to remove ransomware virus and restore files, please continue to read, learn 3 effective methods and how to prevent it in the future. - Best Ransomware Rescue Disk for Data Protection (Free)
To get encrypted files back after ransomware virus attack, you need to create a ransomware rescue disk. The stepwise guide are in the following. - Top Three Easy Methods to Block TCP Port 445 in Windows 10, 7, XP
WannaCry ransomware run amuck recently. It is important to know how to block/disable/close TCP port 445, 135, 139 opened by system on Windows 7/10/11/Server 2003/2008 step by step. - How to Free Up Space on Windows 11 Easily and Safely (3 Ways)
This article describes why free up space on Windows 11 and 3 easy and safe approaches to achieve the goal, including the easiest one. Please read on.